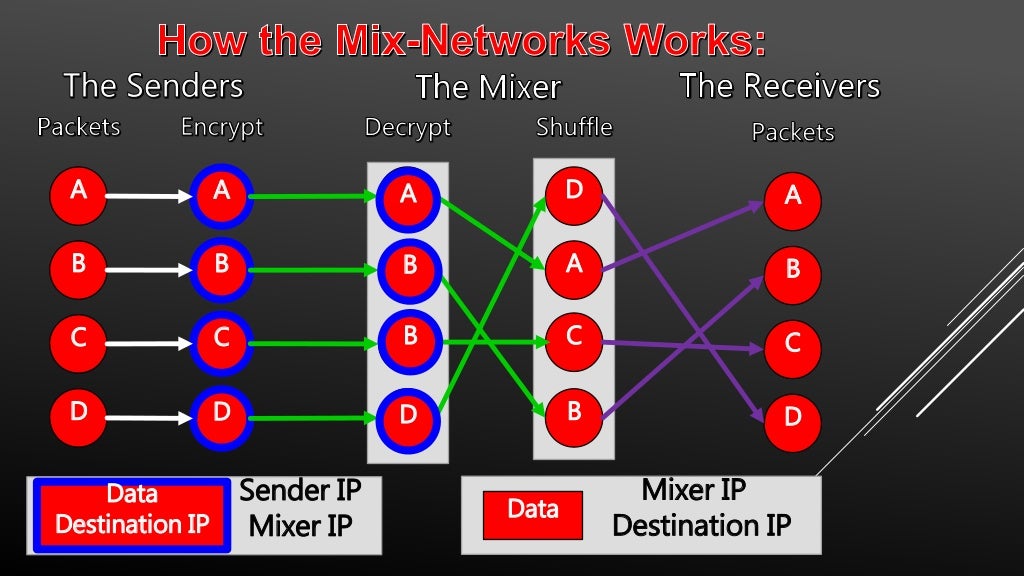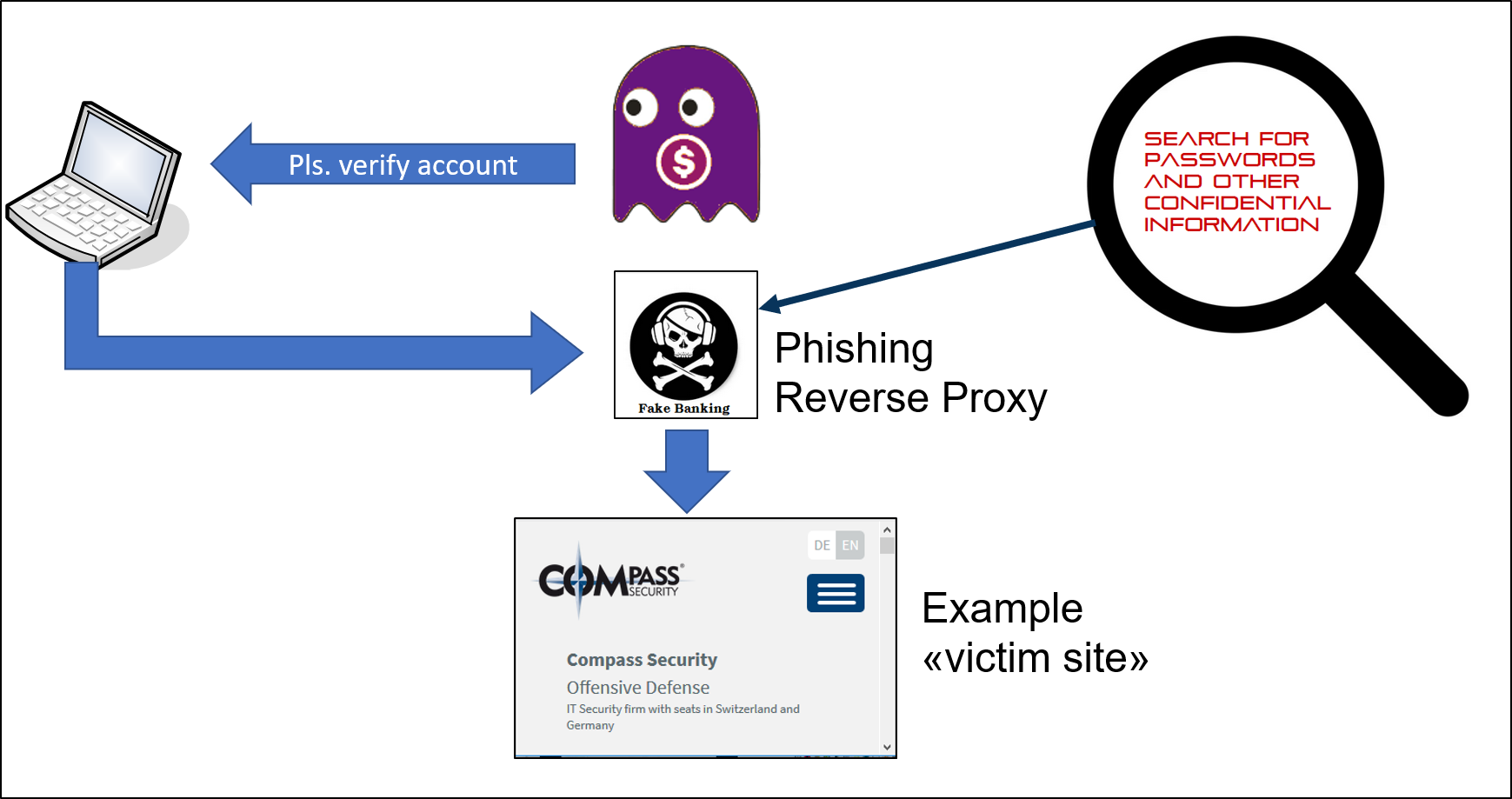
Discussions about the darknet or dark web are typically centered around the Tor network, and the data from breaches, password dumps. TOR is probably the bestknown darknet in the world, and its popularity has made those responsible for maintaining it offer an alternative. Curious how versions of Tor are shifting the Darknet Landscape? Learn the history of Tor & Decentralized Network Security. As a side note, the 1990's were also when Tor, a private Internet browsing network that would later serve as a main connecting point to the dark. Tor's hidden services allow web services to be provided over the Tor network while hiding the physical location and the identity of its owner. Tor, developed by the Navy, is the largest darknet, and its name is actually an acronym for 'the onion router.' Screenshot of tor darknet. Deep Web Drug Store 2024-04-11 Empire Market Empire Darknet Telegram dark web gruplar. pastebin tor links Telegram Groups for Dark. Dark Web Typosquatting: Scammers v. Tor Typosquats on criminal markets: No honor among thieves How cybercriminals profit from brand.
Onion are known as Tor onion services or if you want to be dramatic about it, the dark web. Here's how it all works. Tor Browser Lets. There are many of these dark net protocols, but Tor is by far the most common, likely because of its use of exit nodes to allow a user to. A tainted version of the Tor Browser is targeting dark web market shoppers to steal their cryptocurrency and gather dark markets malta information on their. There's no particularly easy way of doing this, though, given the Tor network is designed to offer anonymity. But by monitoring data signatures. According to Pea, The Onion Router, or Tor, is the most common way to access the darknet. Onion routing allows anonymous browsing and. Dark web spy spy. 8 min read. According to the Tor Project website: Tor is free software and an open network that helps you defend against. Tor, which was initially released as The Onion. Routing project in 2002, was originally created by the tor darknet.. Naval Research Laboratory as a tool. Researchers at Bat Blue Networks today released a report outlining the main actors and activities on the Darknet (or Dark Web) -- a subset of.
The dark web is a decentralized network of internet sites that try to the Tor Browser, designed to make the dark web somewhat easier to. Tor darknet thumbnail. Alexa Rank: 133182. Darknet Markets List 2024. List of all the best dark web markets. Keywords: tor, Onion. Many criminal investigators and analysts have heard of virtual private networks, proxies, and Tor. But, most would not feel comfortable conducting an. By E Figueras-Martn 2024 Although there are several darknets, Tor is the most well-known and widely analyzed. Darknet. Deep Web. Freenet. Connectivity. Content analysis. Defend yourself against tracking and surveillance. Circumvent censorship. Anonymity Online.The Tor Project Support Catal dark markets malaysia (ca. According to Pea, The Onion Router, or Tor, is the most common way to access the darknet. Onion routing allows anonymous browsing and. Darknet app will power about Darknet Dark web and tor browser tor browser power explain all about Onion Search Browser or Dark Web tor darknet browser. The majority of the users on the dark web use the Tor (The Onion Router) browser. A vast number of URLs have domain endings such as. onion, which means.
With an encrypted and anonymous connection, Tor helps you access the unindexed part of the internet known as the dark web. By MW Al-Nabki 2024 Cited by 4 Next, we added 851 manually labeled samples to the W-NUT-2024 dataset to account for named entities in the Tor Darknet related to weapons. Kindle Anonymity Package - 5 Books for the Price of 1!Darknet: The ULTIMATE Guide on the Art of InvisibilityWant to surf. The anonymity-focused Tor Project wants to make darknet sites not just Tor websites are located at this far end of the deep web. Dark Web Typosquatting: Scammers v. Tor Typosquats on criminal markets: No honor among thieves How cybercriminals dark markets luxembourg profit from brand. The majority of the users on the dark web use the Tor (The Onion Router) browser. A vast number of URLs have domain endings such as. onion, which means. Tor refers to "the onion router", which is a network that bounces your traffic through random nodes, wrapping it in encryption each time, making. Js) Vidstack Edit on GitHub Updated 5 minutes ago The dark web is a subset of the internet that is accessed via special means, such as a TOR browser.
Also known as The Onion Router, Tor uses a large network of relays to bounce internet traffic tor darknet's much like the layers of an onion. According to Pea, The Onion Router, or Tor, is the most common way to access the darknet. Onion routing allows anonymous browsing and. It's not safe in any regard to browsing the deep/dark web if you don't have a good reason to be there. If you're using Tor to go on the. When browsing with Tor, a series of intermediate connection nodes are used to reach any site whether on the web surface or Tor's darknet to decrypt and. If you search the net you will see many ways to navigate the deep web using Tor. I'm new to the deep web, but I can't find anything through the hidden wiki. If you use the Tor network regularly, you will want a way to share stuff with your dark web friends. of the conventional web, 8chan aspires to be an. Two typical darknet types are social networks (usually used for file hosting with a peer-to-peer connection), and anonymity dark markets lithuania proxy networks such as Tor via. Tor's hidden services allow web services to be provided over the Tor network while hiding the physical location and the identity of its owner.
Dark Market
Evil Search Engine: not Evil Search Engine is the successor of TorSearch and the Evil Wiki, two of the best search engines to tor darknet search the Darknet. Russian and English, Club2CRD spans a pretty extensive range of offers from malware and exploits to POS devices and hacked accounts. There are significant limitations to Bitcoin and hurdles that would have to be overcome before it could be a daily use payment. The distance between these antenna systems is usually small making it extremely difficult to achieve flawless performance. Monopoly Market aims to stop exit scams by only allowing vouched vendors on their site. The changes would have entailed a complete ban on civilian ownership of category-A firearms and the inclusion of semi-automatic weapons that look like automatic firearms into the category of banned firearms. Bios: Merry Ravenell primarily writes dark fantasy and paranormal fiction, usually with characters that have sharp claws, large fangs, and dangerous appetites. In 2015, the US Financial Crimes Enforcement Network (FinCEN) fined Ripple Labs $700,000 for acting as an unregistered money services business and failing to maintain an adequate anti-money-laundering programme. Altoona school superintendent pleaded guilty Friday in federal court to possessing child pornography involving a sexually explicit image of a 17-year-old girl. I am trying to get as many regular contributors as possible switched to contributor status before we.
“This was someone who was a crack and heroin seller. In fact, Valhalla was closed by LE several weeks before Wall Street Market, but Europol connected both acts into one statement to dark markets liechtenstein emphasize LE success.”
Dark Markets 2024
Luxembourg seems to be the most likely candidate to legalize a recreational framework first. BMG is a firearm, ammunition, and equipment store where you can find a wide range of rifles and guns. Rather than using the central Hypertext Transfer Protocol (HTTP) to communicate, dApps rely on wallet software to interact with automated smart contracts on networks like the Ethereum blockchain. Duplicate listings have been tor darknet removed and prices have been averaged of any duplicates. Common on exchange trading interfaces, a limit order tor darknet is a function to buy or sell an asset at a specific price. It doesn't help that Dark Web users are fighting to protect each other. The group included experts from federal, state, and local agencies; academic researchers; and civil rights advocates.
You can follow us on Linkedin, Twitter , Facebook for daily updates.